Enterprise organizations are interconnected with thousands of mission-critical applications across a complex IT environment. These systems power crucial infrastructure like finance, healthcare, manufacturing, and more. A single security vulnerability in their system can cause major disruptions and financial losses.
Over the years, software supply chain attacks are on the rise, compliance rules are becoming stricter, and technologies like generative AI are introducing new layers of complexity. That is the reason most traditional security methods simply can’t keep up.
That’s why a resilient enterprise application security is more important than ever. It helps organizations stay ahead of evolving risks and protect their entire application ecosystem.
In this guide, you’ll learn the fundamentals of enterprise app security, the real-world challenges teams face, components of enterprise AppSec, and proven best practices that development and security teams can use to safeguard apps at scale.
What is Enterprise Application Security?
Enterprise application security is all about protecting the software that businesses rely on every day. These apps incorporate any software or system an enterprise utilizes to support its business procedure, like enterprise resource planning (ERP) systems, supply chain management (SCM) systems, and customer relationship management (CRM) systems.
These applications help keep operations running smoothly, so keeping them secure is a top priority. Enterprise application security includes:
- Protecting your own code, third-party tools, and open-source software.
- Integrating role-based access control (RBAC) so that only the right people can use sensitive systems to eliminate insider threats.
- Implementing firewalls, encryption, and security testing services to identify potential vulnerabilities.
- Constant monitoring to stay compliant with regulations like GDPR, PCI-DSS, and SOC2.
- Building security into the CI/CD pipelines ensures that issues are caught early, before they become real problems.
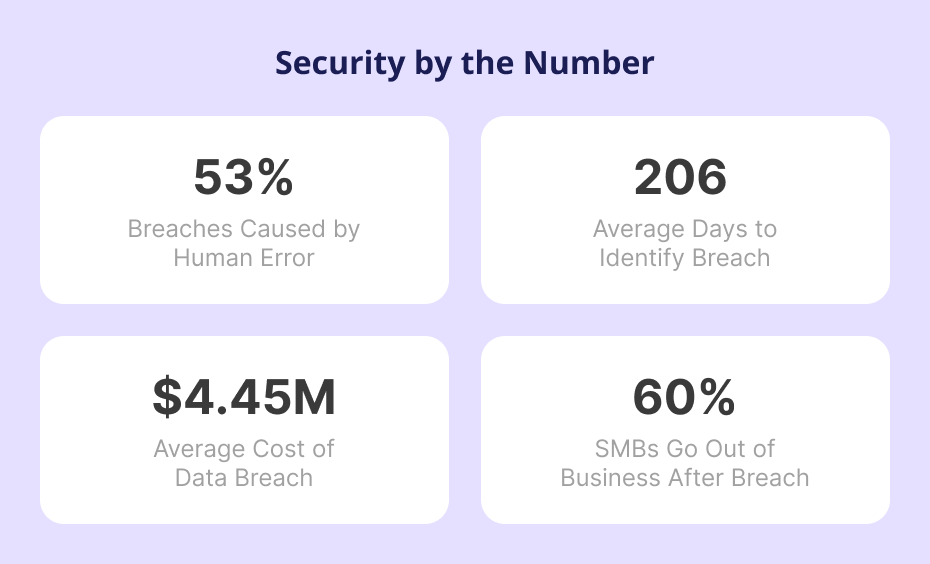
In today’s digital-first world, enterprise apps manage sensitive data such as customer information, financial records, and intellectual property. A single breach can lead to millions in damages. IBM’s Cost of a Data Breach Report 2024 revealed that the global average breach cost has risen to $4.45 million.
This makes security not just a technical requirement, but a strategic business imperative for securing the enterprise.
The goal is to provide future-proof business application security, prevent data leakage, and mitigate the financial and reputational consequences of a security breach.
Why Enterprise App Security Matters?
Digital threats are growing fast, and the global application security services market reached $210 billion, which shows just how serious the financial risks can be. This makes strong enterprise mobile application security imperative, as a breach can impact both the short-term and long-term business objectives.
Let’s examine the five benefits of enterprise application security and how it enhances business operations.
-
Safeguarding Confidential Business Data
Every business handles sensitive information, including customer details, financial records, and proprietary data. It ensures this information stays protected through encryption, access controls, and secure storage.
-
Ensuring Operational Continuity
If a mission-critical system is compromised, it can disrupt major business processes, reduce productivity, and negatively impact revenue. A strong application security assessment eliminates redundancy and increases resilience across your technology stack.
-
Upholding Customer Trust
People trust businesses that protect their data and are reliable. An enterprise application security failure can damage your public relations, leading to a crisis that diminishes user trust and potentially causes churn.
-
Meeting Regulatory Compliance
Industries such as finance and healthcare must adhere to strict data regulations. Regular application security audit helps improve compliance and build trust with auditors.
-
Supporting Scalability and Innovation
Companies that want to adopt an enterprise security program must embrace the latest tools and technologies to ensure that every new feature doesn’t become a new risk. For that, you need to consult with a digital transformation services provider to implement every functionality into their system correctly.
Enterprise Application Security vs. Traditional Application Security (AppSec)
When it comes to protecting applications, both enterprise mobile app security and traditional Application Security (AppSec) play essential roles. But they’re not the same. Let’s take a look at how these two approaches differ:
Aspect | Traditional Application Security | Enterprise Application Security |
| Scope | Focuses on individual apps | Covers the enterprise app platform and infrastructure. |
| Approach | Reactive and fixes issues after they appear | Proactive and prevents issues before they happen |
| Techniques Used | Code reviews, vulnerability scanning and penetration testing | Risk-based prioritization, DevSecOps, shift-left security |
| Complexity Handling | Designed for simpler app structures | Built to manage complex, interconnected systems |
| Security Governance | Limited governance and policies | Strong focus on compliance, policy enforcement, and risk management |
| Scalability | Works for small to mid-size setups | Designed to scale across large enterprises |
| Risk Management | Reactive response to threats | Ongoing, proactive risk reduction across the organization |
Importance of Compliance & Regulations
Enterprise application security is deeply tied to regulatory compliance. Failing to adhere to industry standards can result in massive fines and legal penalties. Key frameworks include:
-
GDPR (General Data Protection Regulation) – Enforces strict privacy laws in the EU.
-
HIPAA (Health Insurance Portability and Accountability Act) – Protects sensitive health information in the US healthcare sector.
-
PCI DSS (Payment Card Industry Data Security Standard) – Mandatory for businesses handling credit card payments.
-
SOC 2 Compliance – Crucial for SaaS and cloud service providers to prove trustworthiness.
A well-documented web application security testing checklist aligned with these standards ensures that organizations minimize application security challenges while staying compliant.
Foundational Components of Strong Enterprise AppSec
Application security for businesses goes far beyond just installing a firewall or running occasional code scans. Real security means building protection into every layer of your systems and software development lifecycle.
From how users log in to how data is stored, each part of your IT environment must be secured thoughtfully. When every layer is designed with safety in mind, it becomes easier to contain problems and prevent them from affecting your entire operation.
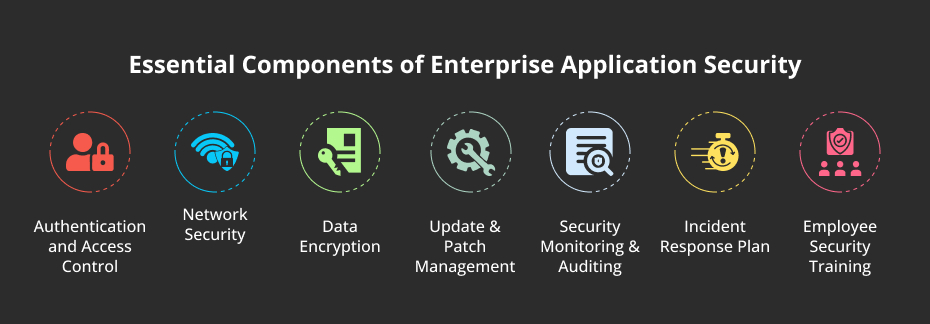
Here’s a breakdown of the essential components that make up a strong enterprise application security framework:
1. Authentication and Access Control
It starts with making sure only the right people can access your systems. Utilize multi-factor authentication (MFA) to verify user identities and implement strict data access controls for enterprise applications based on user roles.
2. Network Security
Firewalls and intrusion detection systems help monitor traffic and block malicious activity. Virtual private networks (VPNs) further protect communication by encrypting data in transit.
3. Data Encryption
Your data needs protection, whether it’s stored or being shared. Encrypt both at-rest and in-transit data, and keep your encryption algorithms up to date to defend against new threats.
4. Update and Patch Management
Outdated software is a common entry point for attackers. You can partner with a legacy software modernization company which can regularly patches and updates all applications, operating systems, and third-party tools to close known vulnerabilities.
5. Security Monitoring and Auditing
Integrate continuous data leakage monitoring to detect unusual activity in your application and system logs. Combine this with regular audits to assess the adequacy of your security for enterprise applications.
6. Incident Response Plan
Be ready for the unexpected. Create a detailed incident response plan and conduct regular simulations to ensure your team knows how to act quickly and effectively. You can perform enterprise application security testing to pinpoint areas for improvement.
7. Employee Security Training
Train your staff on application security best practices so that they recognize phishing, social engineering, and other risks. Ongoing training sessions keep staff informed about the latest cybersecurity threats and the mitigation plan across your organization.
Common Vulnerabilities in Enterprise Applications
Enterprise software is great for driving efficiency, but it can also be vulnerable to cyber threats. Hackers are constantly on the lookout for weaknesses, especially in areas where data is entered by users or transferred between systems. These gaps often go unnoticed due to skipped code reviews or delayed software patches, making them prime targets for cybercriminals.
Therefore, it’s vital to first understand the common types of threats in enterprise apps. Knowing what to look for helps you build smarter defenses and conduct more targeted enterprise app security testing. Let’s look at them.
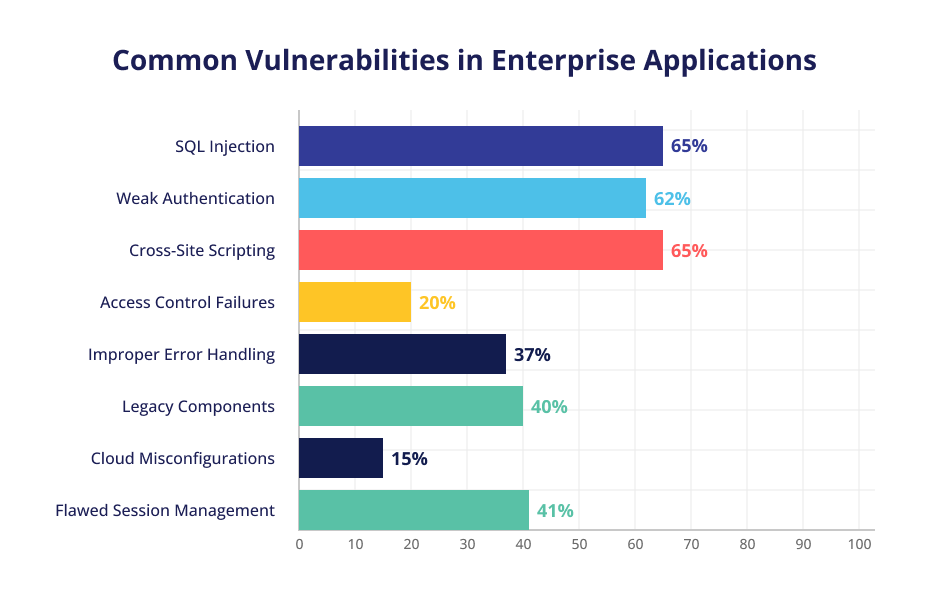
1. SQL Injection Attacks
This threat occurs when an attacker inserts malicious SQL statements into input fields, potentially gaining full access to your database. To prevent SQL injection, use parameterized queries or query parameters and validate all user inputs to block harmful commands.
2. Weak Authentication Methods
Using simple passwords or having poor login setups makes it easy for attackers to break in. Implementing multi-factor authentication (MFA), enforcing complex password rules, and monitoring session activity are key steps to strengthening access controls.
3. Cross-Site Scripting Risks
Cross-Site Scripting (XSS) happens when attackers inject malicious scripts into web pages. These scripts can steal data such as session tokens or login credentials. Applying an enterprise web application security program, sanitizing inputs, and encoding outputs are effective ways to prevent such attacks.
4. Access Control Failures
When access controls are weak, users might end up with permissions they shouldn’t have. This could let them view or change sensitive data. Using role-based access controls (RBAC), managing identities carefully, and regularly reviewing permissions can help mitigate these risks.
5. Improper Error Handling
Sometimes, error messages reveal too much information, such as system details or database structures. This can help attackers plan their next move. To stay safe, cybersecurity for enterprise applications should limit the display of error messages and maintain detailed logs solely for developers, not for public view.
6. Legacy Components and Libraries
Using third-party libraries is common, but older versions may contain known vulnerabilities. That’s why it’s essential to keep libraries up to date through legacy application modernization. Automation tools can flag outdated code and notify developers before issues arise, preventing problems from occurring.
7. Cloud Misconfigurations
As more businesses migrate to the cloud, simple mistakes such as leaving storage buckets open can lead to data leaks. Seeking assistance from a leading cloud migration services provider can be beneficial in this regard. They can upgrade enterprise application security via regular audits, configuration tools, and alerts that help identify these issues early.
8. Flawed Session Management
If session IDs aren’t refreshed at login or expired after logout, attackers can hijack them. Secure cookies, token rotation, and shorter session times are smart ways to protect user data. Auditors often look at the enterprise application security checklist for robust session management measures to safeguard user data.
Key Requirements for Enterprise Application Security
Protecting enterprise software isn’t just about keeping out intruders. In today’s rapidly evolving digital world, security must be proactive, structured, and adaptable. That’s why having a clear set of enterprise security requirements is essential. These guidelines help shape how your applications are built, updated, and scaled, keeping you aligned with standards such as GDPR, HIPAA, PCI DSS, and other relevant regulations.
Let’s look at the key requirements that should guide your enterprise security strategy:
-
Regulatory Compliance Alignment
Regulations like SOC 2, ISO 27001, and regional privacy laws require regular audits and risk assessments. Instead of treating compliance as a last-minute hurdle, it should be built into your enterprise software design and development process. This helps avoid penalties and builds trust with users and partners.
-
Effective Change Management
Every update introduces potential risks. Strong change management ensures that all modifications undergo accessibility testing, thorough documentation, and peer review. This minimizes errors and prevents unintended security gaps.
-
Comprehensive Audit Trails Logging
Logs track who did what and when, which is crucial during any security investigation. Storing logs securely and encrypting them adds a layer of security. When combined with continuous monitoring, audit trails help spot unusual activity early.
-
Data Privacy Controls
Privacy builds trust. From encrypting sensitive data to masking personal information, you must follow local laws and industry best practices for application security. Tokenization and DLP tools can help ensure private data stays private.
-
Penetration Testing and Ethical Hacking
Automated tools are great, but red teaming can dig deeper. They test your systems like real attackers would, revealing issues that machines might miss, especially logic flaws or complex attack chains.
Enterprise Application Security Best Practices
To keep enterprise applications safe, it’s essential to follow a few best practices that integrate security into your everyday workflow. Here are six key ones to get started with:
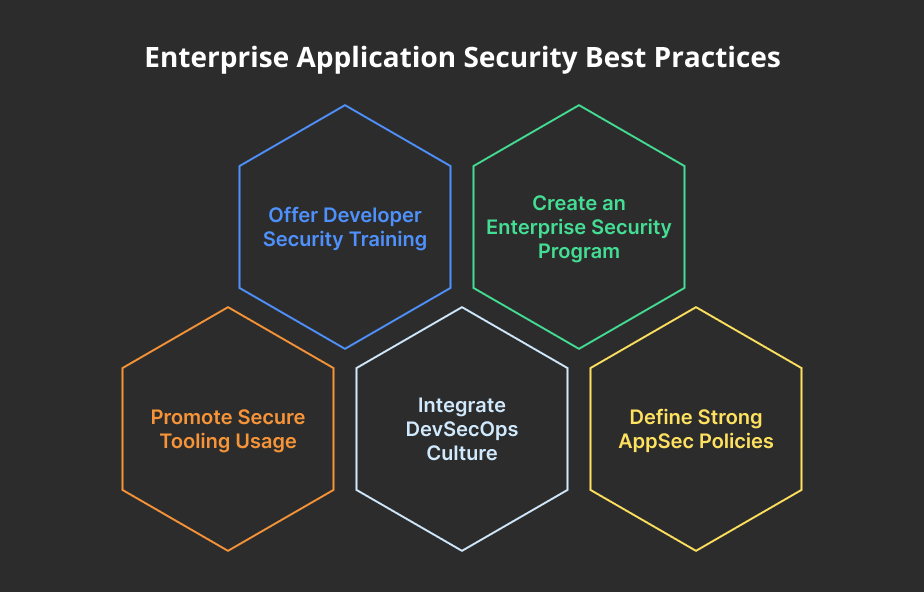
-
Perform Application Risk Profiling
Take a close look at all your applications to spot which ones are most vulnerable. This helps you focus on the areas that need the most attention.
-
Offer Developer Security Training
Security isn’t just for IT teams. Enterprise application developers should learn how to write secure code from the outset and throughout the planning, development, and deployment phases.
-
Create an Enterprise Security Program
Create a team of “security champions” within your developers. They’ll help spread awareness and bridge the gap between dev and security teams.
-
Promote Secure Tooling Usage
Add enterprise application security tools to your development pipeline. Automating security checks saves time and catches issues early.
-
Integrate DevSecOps Culture
Bring security into every stage of development with DevSecOps services. Make it a shared effort across teams, not just a final check.
-
Define Strong AppSec Policies
Have clear rules for secure coding, authentication, and access controls. This keeps your apps safe from the ground up.
Enterprise Application Security Challenges
As enterprise app development speeds up, thanks to larger codebases and tools like GenAI, maintaining app security becomes increasingly complex. Security teams now face both old and new challenges, including scattered tools and staffing shortages, as well as AI-generated vulnerabilities and growing compliance demands.
Beyond misconfigurations and vulnerabilities, enterprises face advanced risks such as:
-
Supply Chain Attacks: Insecure third-party components and open-source libraries can introduce backdoors.
-
Insider Threats: Privileged employees misusing access rights, either maliciously or accidentally.
-
Shadow IT: Teams are adopting unauthorized applications that bypass enterprise security controls.
-
Zero-Day Exploits: Attacks targeting unknown vulnerabilities with no available fixes.
These web application security risks highlight why businesses must implement proactive monitoring, risk assessments, and enterprise access control systems to prevent unauthorized exposure.
Below is a breakdown of the major application security challenges and how to tackle them:
Challenge | What’s the Problem? | Solution |
| Too Many Tools, High Costs | Juggling multiple security tools creates confusion, gaps, and high costs | Implement ASPM to bring tools together and reduce complexity. |
| Code Change Blindspots | It’s challenging to determine how code updates impact security, resulting in delays and missed issues. | Use Change Impact Analysis (CIA) to find risks fast and prevent problems early. |
| Open-Source & Supply Chain Risks | Hidden threats in third-party code are often missed. | Utilize advanced SCA tools with real-time tracking to identify more nuanced issues. |
| Tough Compliance Reporting | Manual reporting is time-consuming and inefficient. | Automate compliance tracking and simplify audit reporting. |
| Risk Prioritization & Remediation | Too many alerts, and no clarity. Teams receive numerous warnings but lack clear priorities. | Integrate AI to highlight the most critical risks, enabling developers to address the most pressing issues first. |
Enterprise AppSec Tools and Technology Examples
When it comes to enterprise application modernization, having the right security tools is just as important as following good coding practices. Together, they help keep sensitive data safe and reduce the risk of cyberattacks. Let’s break down some key tools used in enterprise application security:
-
SAST (Static Application Security Testing)
Static application tools look at your source code before the app runs. It helps catch issues early, such as SQL injections or cross-site scripting, by scanning for vulnerabilities within the code itself.
-
DAST (Dynamic Application Security Testing)
DAST tools check the application while it’s running. It simulates real-world attacks to find problems with authentication, session management, or input validation.
-
ASPM (Application Security Posture Management)
ASPM tools connect the dots between various security tools. It gives a full view of risks and helps teams prioritize what needs fixing first based on real threats.
-
SCA (Software Composition Analysis)
Software composition analysis focuses on third-party and open-source components. It identifies known vulnerabilities, allowing developers to update or replace risky libraries before they cause harm.
Emerging Trends & Future Outlook
The future of enterprise application security will be shaped by:
-
AI/ML in Cybersecurity
Detecting anomalies and zero-day threats faster than human analysts.
-
Cloud-Native Security
Protecting applications built on Kubernetes, containers, and serverless infrastructure.
-
Automated Incident Response
Using orchestration to reduce breach response time from weeks to hours.
-
Regulatory Tightening
New policies like the EU’s AI Act and NIS2 Directive will push stricter compliance.
Enterprises that embrace automation, AI, and enterprise access control frameworks will be far better prepared to meet evolving application security challenges.
How SparxIT Helps With Enterprise Application Security?
SparxIT is a leading enterprise app development company, simplifying and enhancing application protection. We work seamlessly with popular tools, such as IDEs, CI/CD pipelines, and version control systems so to integrate security seamlessly into your existing workflow.
Our enterprise application security services can identify and resolve security issues promptly, preventing them from escalating into significant problems. This helps reduce risks and keeps enterprise applications safer from the start.
SparxIT’s solutions include fast and reliable vulnerability scans, detailed reporting, ongoing developer training, and the ability to set custom security policies. Plus, we integrate easily with the tools developers already use every day.
Final Thoughts
Keeping business applications secure isn’t a one-time fix; it’s an ongoing process that involves utilizing innovative tools, providing employee training, and implementing solid planning. As cyber threats continue to evolve, companies must remain adaptable and continually enhance their defenses.
Taking assistance from a top cybersecurity consulting services provider helps enterprises mitigate risks, protect sensitive data, and ensure critical systems remain operational smoothly. Ultimately, staying ahead of potential threats is the most effective way to safeguard the digital tools and information that drive your business forward.

Partner with Experts
Frequently Asked Questions
How to modernize enterprise app security without downtime?







You can modernize application security in phases by using blue-green deployments, rolling updates, or feature flags. This way, changes happen behind the scenes, users stay unaffected, and your application keeps running without interruptions.
How much does it cost to modernize enterprise application security?












The cost to modernize enterprise application security varies widely, ranging from $40,000 to $150,000 or more, depending on the project's complexity and scope. Factors like the size and complexity of the legacy system, the specific modernization approach, and the extent of testing and validation all influence the final cost.
How does DevSecOps help in enterprise application security modernization?












DevSecOps blends security into every stage of development. Instead of checking for risks at the end, it automates testing early. This speeds up delivery, catches issues sooner, and reduces the chance of major vulnerabilities.
What tools are used in modern enterprise application security?












Common tools include SAST for code analysis, DAST for live testing, SCA for open-source checks, and ASPM for overall visibility. These tools work together to detect threats early and maintain system security throughout the development process.
How does application security differ for cloud-based enterprise apps?












Cloud apps require additional layers of security, including encryption, identity access control, and proper configuration management. Since resources are shared and remote, it’s crucial to monitor for misconfigurations and follow cloud-specific security best practices.



